Introduction
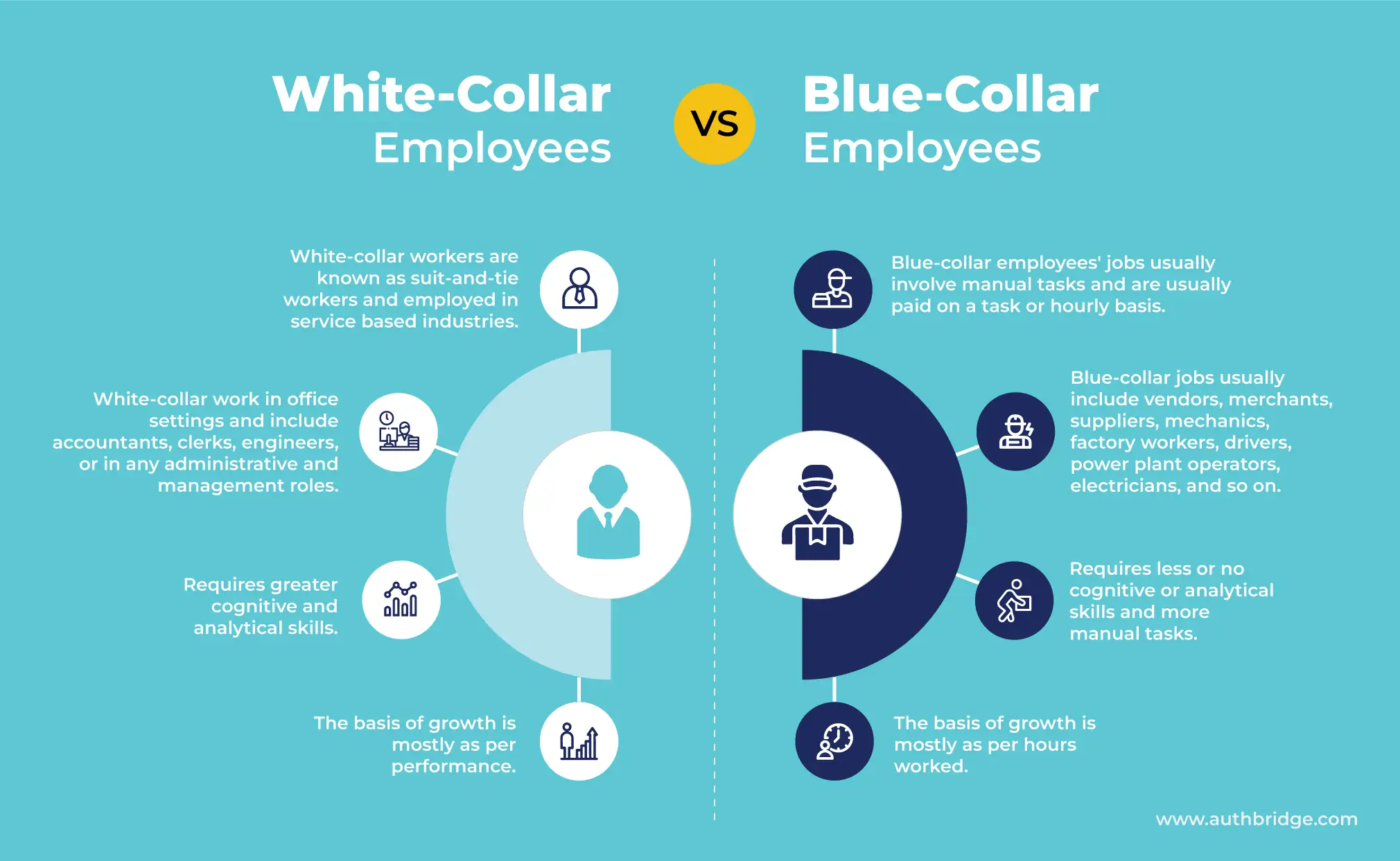
Know Your Customer (KYC) is a process of verifying the identity of customers to prevent financial crimes such as money laundering, terrorist financing, and identity theft. KYC is mandatory for banks, insurance companies, mutual funds, and other financial institutions to comply with regulations and mitigate risks.
Video KYC is a technology-driven solution that has revolutionised the KYC process by allowing customers to complete the verification process remotely. Video KYC offers a faster and more convenient way of performing KYC checks, eliminating the need for physical documents.
The global e-KYC market is expected to reach USD 1,568.95 Million by 2027, growing at a CAGR of 23.4% during the forecast period from 2020-2027. The increasing adoption of digitalization and the rising demand for efficient KYC processes are the key factors driving the growth of the e-KYC market.
Exploring the Functioning of Video KYC: A Tentative and Informative Perspective
KYC (Know Your Customer) is a process that banks and financial institutions use to authenticate customer identities. Video verification offers a more efficient and secure alternative to traditional methods, which explains its growing popularity among institutions.
How to do Video KYC
Step 1: Registration
To access bank accounts, loans, and insurance policies, banks now mandate customer registration for various purposes, including ID verification and loan applications. Registration is essential for maintaining trust and security during the customer onboarding process. Video KYC enhances the customer experience by making onboarding faster.
Step 2: Profile Input
Banks collect profile information by gathering essential details, such as customer names, security numbers, contact numbers, and addresses. Video KYC has become one of the most efficient and secure ways of conducting KYC due to its numerous advantages, including speed, convenience, accuracy, scalability, and compatibility with advanced mobile money solutions.
Step 3: Face-to-Face Virtual Call
Video KYC enables identification through video footage rather than solely relying on photo IDs. This technology has transformed how bank officials verify customer identities, making it so reliable that many banks now consider it their primary method of identity verification. Video KYC is not only less time-consuming and expensive, but it also minimizes the risk of fraud or personal data misuse by customers.
Step 4: Verification
Bank executives can virtually verify customers by examining physical documents during a call. Customers must present all necessary physical documents, such as address proof, ID proof, and security numbers, to finalize the verification process.
Advantages of Video KYC Adoption
Bank executives can virtually verify customers by examining physical documents during a call. Customers must present all necessary physical documents, such as address proof, ID proof, and security numbers, to finalize the verification process.
Advantages of Video KYC Adoption
The integration of video KYC as a preferred customer authentication method has brought numerous benefits to various financial sectors. Here are some of the specific advantages for banks, insurance companies, mutual funds, and Non-Banking Financial Companies (NBFCs):
Banks
Streamlined account opening
Video KYC for banks simplifies and expedites the account opening process by eliminating paperwork and reducing manual input.
Enhanced security
Banks can better secure customer data and reduce the risk of fraud by implementing video KYC, which uses advanced technologies such as AI and liveness detection.
Improved compliance
The adoption of video KYC enables banks to better adhere to regulatory requirements and minimize the risk of non-compliance penalties.
Insurance Companies
Accelerated policy issuance
Video KYC for insurance companies reduces the time required for customer verification, leading to faster policy issuance and improved customer satisfaction.
Lower operational costs
By implementing video KYC, insurance providers can reduce the expenses associated with traditional verification methods, such as physical document storage and manual processes.
Better customer retention
The ease and convenience of video KYC increase policyholders’ satisfaction, thus promoting loyalty and retention.
Mutual Funds
Quicker onboarding
Video KYC for mutual funds streamlines the investor onboarding process, providing a seamless experience for new clients.
Wider reach
With video KYC, mutual funds can cater to a broader audience, including investors in remote areas, who may not have easy access to physical branches or documentation centres.
Enhanced investor engagement
By reducing barriers and simplifying the authentication process, video KYC fosters increased engagement and satisfaction among investors.
NBFCs
Expedited loan processing
Video KYC for NBFCs enables faster identity confirmation and document verification, resulting in quicker loan processing times.
Strengthened data security
NBFCs can mitigate data breaches and identity theft risks by leveraging the cutting-edge technology provided by video KYC.
Improved compliance and risk management
Adopting video KYC helps NBFCs comply with regulatory requirements and manage risks more effectively, minimizing potential non-compliance penalties.
The advantages of video KYC for banks and financial institutions are evident – it is quicker, more straightforward, and safer! By employing video technology, institutions can authenticate customer identities using biometric parameters such as facial recognition and retinal scanning.
Contrasting Video KYC with Traditional KYC: Understanding Key Differences
Speed and convenience
- Traditional KYC: Manual customer identification programs can take weeks, leading to customers abandoning the process mid-way.
- Video KYC: A digital version that is faster, more secure, and cost-effective, delivering real-time results.
Paperwork and processing
- Traditional KYC: Requires physical document submission and involves a cumbersome paperwork process.
- Video KYC: Eliminates paperwork, streamlining the verification process through digitization.
Customer onboarding
- Traditional KYC: Customers must visit the company physically to submit identity documents, leading to delays in account opening.
- Video KYC: Allows customers to register and onboard remotely, significantly improving convenience and efficiency.
Security and risk assessment
- Traditional KYC: Faces potential security lapses and higher risk due to manual handling of sensitive customer data.
- Video KYC: Provides a more secure process by leveraging advanced technology, ensuring better risk management.
Role of Verification in the Video KYC Journey
Enhancing the efficiency and security of customer onboarding with digital verification techniques:
Identity Verification: In the Video KYC procedure, consumers must provide legitimate government-issued IDs like Aadhaar or PAN cards, which are checked using sophisticated optical character recognition (OCR) technology to reduce fraud.
Identity Verification
In the Video KYC procedure, consumers must provide legitimate government-issued IDs like Aadhaar or PAN cards, which are checked using sophisticated optical character recognition (OCR) technology to reduce fraud.
Liveness Detection
Blink testing, facial tracking, and motion analysis are used to verify the customer’s presence during the Video KYC session to avoid identity theft and unauthorised access.
Geolocation Verification
It is used to comply with regulatory standards and provide easy onboarding for qualified consumers.
Secure Data Storage
As customer data is sensitive and requires stringent security measures, Video KYC service providers implement robust data encryption and secure storage solutions to protect against unauthorised access and data breaches.
Compliance with Regulations
Video KYC reduces the risk of non-compliance fines and maintains financial ecosystem confidence by automating the verification process.
AuthBridge excels in streamlining KYC processes for financial institutions by offering comprehensive Video KYC solution, leveraging advanced AI-driven verification and innovative liveness detection techniques. By employing geolocation validation and robust compliance management, AuthBridge ensures an optimised onboarding experience that adheres to regulatory standards, mitigates risks of fraud, and strengthens trust in the financial ecosystem.
Conclusion
The shift from traditional KYC to video KYC presents a promising future for banks, financial institutions, and businesses dealing with money. The benefits of this digital transformation are evident in its increased efficiency, reduced costs, enhanced security, and improved customer satisfaction. As technology continues to evolve, the scope of video KYC will likely expand further, incorporating even more advanced features to optimise the verification process. Thus, arising the need for a technology partner that offers KYC solutions for BFSI sector to make the verification and onboarding journey faster and smoother. Embracing video KYC’s potential not only streamlines the customer onboarding experience but also supports a thriving, secure, and compliant financial ecosystem, ultimately leading to a brighter and more progressive future for all stakeholders involved.