Overview of the Risk Management Lifecycle
In the rapidly globalizing economy of India, businesses increasingly rely on third parties for a broad spectrum of operations, from supply chain logistics to IT services. This reliance, while boosting efficiency and market reach, also exposes companies to a variety of risks including cyber threats, regulatory non-compliance, operational failures, and reputational damage. In this context, Third-Party Risk Management (TPRM) becomes crucial, not only for compliance with India’s stringent regulatory environment but also for safeguarding against operational and strategic vulnerabilities.
TPRM involves a continuous lifecycle that includes identifying, assessing, controlling, and monitoring third-party risks. A strategic approach to this lifecycle ensures that businesses can maintain robust relationships with third parties while safeguarding their assets and reputation. This lifecycle is especially pertinent in India, where the diverse and dynamic nature of the market necessitates a flexible yet comprehensive approach to risk management.
Understanding Third-Party Risks in India
Types of Third-Party Risks
Third-party risks can broadly be categorized into several types including operational, financial, legal, reputational, and cyber. In the Indian context, regulatory compliance risks are particularly significant given the country’s evolving legal framework around data protection, financial transactions, and corporate governance. Understanding these risk categories is the first step in developing an effective TPRM strategy.
The Indian Business Ecosystem and External Partnerships
The unique aspects of India’s business ecosystem, such as its regulatory environment, market dynamics, and the nature of external partnerships, play a critical role in shaping third-party risk profiles. The heavy reliance on outsourcing in sectors like IT and manufacturing, coupled with India’s push towards digital transformation, amplifies the need for a tailored approach to TPRM that can navigate the intricacies of the Indian market.
Developing a Robust TPRM Strategy
Establishing a Governance Framework
A governance framework lays the foundation for effective TPRM by defining roles, responsibilities, and accountability structures. For Indian companies, this involves creating a TPRM committee or function that works in close coordination with all business units involved in third-party engagements. This committee is responsible for setting policies, standards, and processes that align with both Indian regulatory requirements and international best practices.
Key Elements:
- Policy and Procedure Development: Establishing clear TPRM policies and procedures that define how third-party risks are identified, assessed, managed, and reported.
- Roles and Responsibilities: Clearly delineating TPRM roles across the organization to ensure accountability.
- Reporting and Escalation Protocols: Setting up mechanisms for reporting risks and escalating them through the appropriate channels.
Conducting Thorough Due Diligence
Due diligence is the first line of defense in identifying potential risks from third-party engagements. This involves a comprehensive assessment of the third party’s business practices, financial health, legal compliance, and cybersecurity posture.
Due Diligence Checklist:
- Business and Operational Analysis: Evaluation of the third party’s operational capabilities, business continuity plans, and service delivery models.
- Financial Assessment: Review of financial statements and credit ratings to assess financial stability.
- Compliance and Legal Verification: Verification of adherence to Indian laws and regulations, including labor laws, data protection statutes, and anti-corruption standards.
- Cybersecurity Evaluation: Assessment of the third party’s cybersecurity frameworks, incident response plans, and data protection measures.
Regular Risk Assessments and Audits
Ongoing risk assessments and periodic audits are vital to understand the evolving risk landscape associated with third parties. This includes not just initial assessments but regular monitoring and reevaluation to catch any changes in the third party’s operations or risk profile.
Assessment Frequency and Criteria:
- Annual Risk Assessments: Conducting comprehensive risk assessments at least annually or as dictated by significant changes in the third party’s operations or the regulatory landscape.
- Continuous Monitoring: Implementing continuous monitoring mechanisms to detect real-time risks, especially for critical third-party relationships.
- Audit Rights: Securing the right to audit third parties through contractual agreements, allowing for on-site evaluations of compliance and risk management practices.
Mitigation Strategies and Best Practices
Contractual Safeguards and Compliance Clauses
Contracts with third parties should include specific clauses that address compliance with Indian regulations, data protection, and cybersecurity standards. These clauses serve as legal safeguards, ensuring that third parties are legally bound to uphold the standards required by the contracting company.
Example Clauses:
- Compliance with Laws: Clause requiring the third party to comply with all applicable laws and regulations.
- Data Protection: Specific requirements related to the handling, storage, and transmission of sensitive data.
- Right to Audit: Provision allowing periodic audits of the third party’s practices and compliance.
Implementing Continuous Monitoring Systems
Continuous monitoring of third-party activities helps in the early detection of potential risks and breaches. Utilizing technology solutions that provide real-time insights into third-party operations is crucial for this purpose.
Technological Tools:
- Third-Party Risk Management Software: Tools that automate the collection and analysis of third-party data, offering dashboards and alerts for risk monitoring.
- Cybersecurity Monitoring Tools: Solutions that monitor the cybersecurity posture of third parties, detecting vulnerabilities and breaches.
Effective Incident Response and Recovery Plans
Having a structured incident response and recovery plan ensures that any issues arising from third-party engagements can be addressed swiftly and efficiently, minimizing potential impacts.
Plan Components:
- Incident Identification and Assessment: Procedures for the quick identification and assessment of an incident’s impact.
- Communication Strategy: Defined communication protocols, both internal and with the third party, to manage the incident effectively.
- Recovery and Remediation Plans: Steps for recovering from the incident and remedial actions to prevent future occurrences.
Leveraging Technology for TPRM
The integration of advanced technologies like AI and data analytics can significantly enhance the efficiency and effectiveness of TPRM processes. These technologies can automate risk assessments, monitor third-party activities, and provide predictive insights into potential risk areas.
Technological Advancements:
- AI and Machine Learning: Tools that utilize AI can analyze vast amounts of data to identify patterns and predict potential risks from third-party engagements.
- Blockchain: Offers a secure and transparent method for managing contracts and monitoring compliance, particularly in supply chain management.
Navigating Regulatory Requirements
Compliance with Indian regulations and international standards is a cornerstone of effective TPRM. Indian businesses must stay abreast of regulatory changes and ensure that their TPRM strategies are compliant with these requirements.
Regulatory Frameworks:
- Data Protection and Privacy: Adherence to the Personal Data Protection Bill (when enacted) and global data protection regulations like GDPR for international engagements.
- Financial Regulations: Compliance with RBI guidelines for financial institutions and adherence to anti-money laundering (AML) standards.
Case Studies and Real-World Examples
Case Study 1: A Leading Indian Bank and its TPRM Transformation
A top Indian bank revamped its TPRM framework to address regulatory findings and enhance its risk management capabilities. The bank implemented a comprehensive TPRM platform, integrated continuous monitoring tools, and established a centralized risk management function. This transformation led to improved risk visibility, compliance, and operational efficiency.
Case Study 2: Data Breach Incident at an Indian IT Service Provider
An IT service provider suffered a data breach due to vulnerabilities in a third-party software. The incident led to significant financial and reputational damage. The company responded by enhancing its third-party risk assessments, particularly in cybersecurity, and implementing stricter due diligence processes for software vendors.
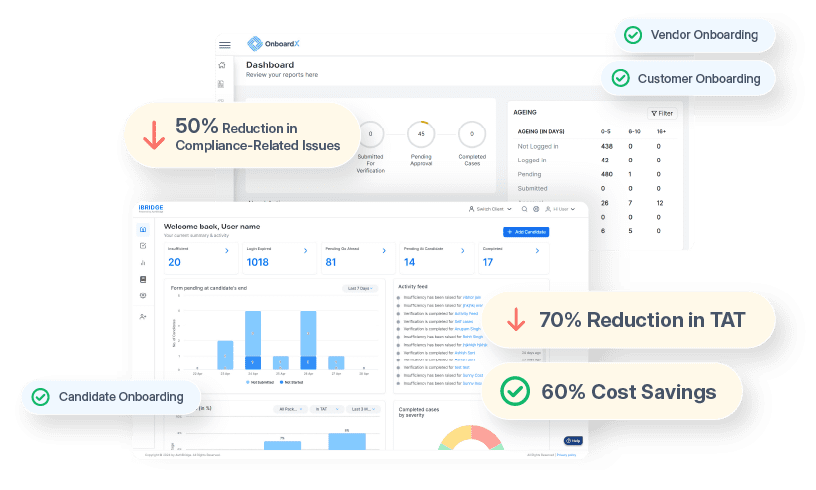
OnboardX By AuthBridge
Welcome to the Future of Vendor Management, OnboardX: The Comprehensive Platform for end-to-end Third-Party Onboarding and Verification. Say goodbye to the hurdles of inefficiency, data disparities, and regulatory complexities.
Adopt a path of automated processes, scalable operations, and cutting-edge analytics to elevate your vendor relationship management to new heights.
As leaders in the world of BGV and due-diligence, our one stop onboarding solution aims to provide seamless onboarding to organisations by offering features such as:
- Case approval workflow with payment and contract signing
- Custom communication options in emails and WhatsApp
- 160+ real-time checks and verifications
- Personalized and customizable solution
- Seamless API integration
- Fully automated journey with multiple touch points and clear visibility
Conclusion
Third-Party Risk Management is an ongoing journey that requires constant vigilance, adaptation, and strategic planning, especially in a complex market like India. By developing robust TPRM frameworks, leveraging technology, and adhering to regulatory requirements, Indian businesses can mitigate third-party risks effectively. As the business ecosystem continues to evolve, so too will the strategies for managing third-party risks, highlighting the importance of a proactive and dynamic approach to TPRM.