Introduction
Effective vendor data management is crucial for businesses to ensure seamless operations, enhance supplier relationships, and maintain compliance with regulatory requirements. Accurate and organized data allows companies to evaluate vendor performance, streamline procurement processes, and mitigate risks associated with supplier interactions.
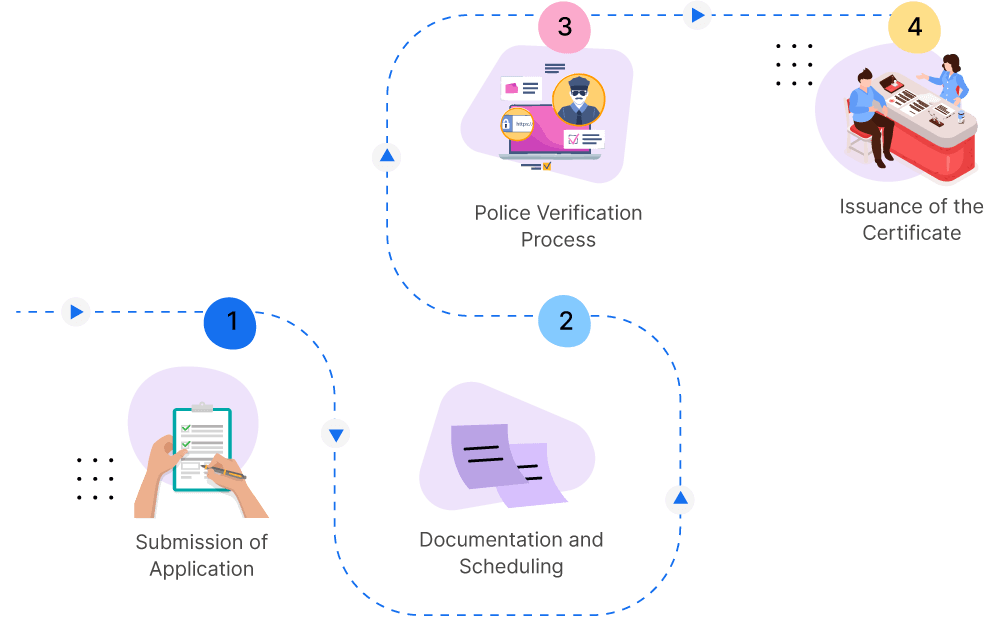
Overview of Document Submission in Vendor Management
Document submission is a key aspect of vendor management that involves the systematic handling, filing, and retrieval of essential documents such as contracts, invoices, compliance certificates, and performance assessments. Developing a structured approach to document management helps businesses maintain transparency, support audits, and foster trust with stakeholders.
Setting Up a Robust Vendor Data Collection System
Designing a Structured Data Collection Framework
To effectively manage vendor data, businesses need to establish a structured data collection framework that encompasses all critical aspects of their interactions with suppliers. This framework should outline:
- Key Data Points to Collect: Such as vendor contact information, tax identification numbers, service/product details, pricing, payment terms, and performance metrics.
- Data Collection Methods: Define whether data will be collected through automated systems, forms, direct inputs from vendors, or a combination of these methods.
- Data Update and Maintenance Protocols: Regular updating and maintenance procedures to ensure data remains current and accurate.
Example Table: Key Data Points for Vendor Management
| Data Category | Specific Data Points |
|---|---|
| Identification | Vendor name, ID, address |
| Financial | Payment terms, credit limits, billing details |
| Operational | Service descriptions, delivery timelines |
| Compliance | Tax documents, certification statuses |
Leveraging the right tools and technologies is crucial for efficient data collection and management. Software solutions like Enterprise Resource Planning (ERP) systems and Vendor Management Systems (VMS) can automate data entry, reduce errors, and provide real-time access to vendor information. Cloud-based platforms offer scalability and accessibility, ensuring data is available across multiple departments and locations.
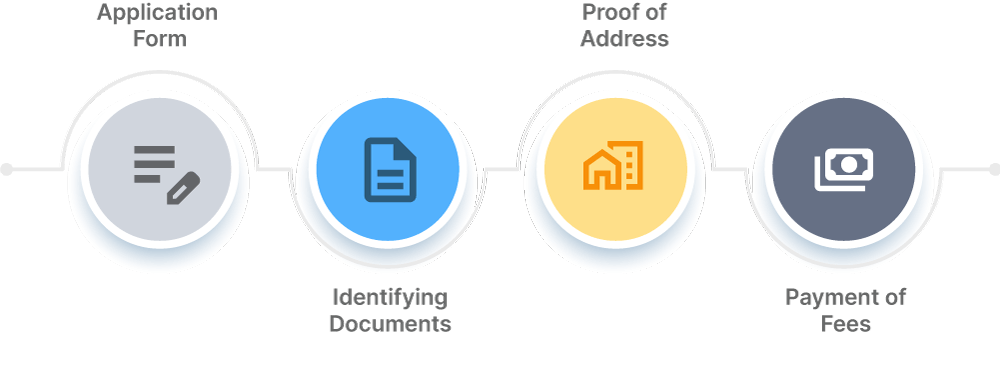
Essential vendor documentation to collect:
- Non-disclosure agreements (NDAs): These are legal contracts that outline confidential information that parties agree not to disclose to others. NDAs are crucial for protecting sensitive business information shared between the vendor and the client.
- Necessary business licensing: This refers to licenses, permits, or certifications required for the vendor to conduct its business legally, such as a business license, professional license, or industry-specific permits.
- Reports on sustainable sourcing practices: These reports detail how the vendor obtains its materials or products in an environmentally and socially responsible manner, showcasing efforts to minimize ecological impact and support fair labor practices.
- Insurance policies: This includes proof of insurance coverage held by the vendor, such as liability insurance, workers’ compensation insurance, or professional indemnity insurance, depending on the nature of the vendor’s operations.
- Financial records and credit history: These documents provide insights into the vendor’s financial health, including balance sheets, income statements, cash flow statements, and credit reports, helping assess the vendor’s stability and reliability.
- Details on regulatory compliance: This includes documentation proving that the vendor complies with relevant laws, regulations, and industry standards governing its operations, such as data privacy regulations, safety standards, or product compliance requirements.
- Certifications related to security measures: These certifications demonstrate the vendor’s adherence to industry-standard security protocols and practices, ensuring the protection of sensitive data and systems from cyber threats.
- Tax documentation, including forms and identification numbers: This encompasses all tax-related paperwork, such as tax identification numbers (e.g., EIN in the U.S.), tax registration certificates, and completed tax forms required by relevant authorities.
- ACH forms for payment processing: These forms authorize the Automated Clearing House (ACH) to electronically transfer funds between bank accounts, facilitating payment processing between the vendor and the client.
- Proof of company ownership: This refers to documents demonstrating the legal ownership of the vendor entity, typically through incorporation papers, partnership agreements, or other official records establishing ownership structure.
- Supplier diversity certifications: These certifications demonstrate a vendor’s commitment to diversity and inclusion in its supply chain, often indicating that the vendor is minority-owned, woman-owned, veteran-owned, or a small business.
- Information on subcontractors, outsourced functions, and fourth-party involvements: This involves disclosing any subcontractors or third-party entities involved in delivering products or services on behalf of the vendor, along with their roles and responsibilities.
Document Management and Submission Protocols

Standardizing Document Submission Processes
Creating standardized processes for document submission helps in maintaining consistency and reducing confusion among vendors. Guidelines should include:
- Submission Deadlines: Clearly defined timelines for regular submissions such as invoices and irregular submissions like compliance documents.
- Format Requirements: Specifications on document formats to ensure compatibility and readability across systems.
- Submission Channels: Designated channels (e.g., email, online portals) that streamline the submission process and support tracking.
Secure Storage and Accessibility of Vendor Documents
Secure and organized storage of vendor documents is essential for protection against data breaches and for ensuring quick accessibility when needed. Implementing digital document management systems that feature encryption, user authentication, and easy retrieval capabilities is vital.
Ensuring Compliance and Accuracy
Legal Requirements for Document Submission and Data Storage
Businesses must adhere to legal requirements related to document retention, data protection, and privacy laws, which vary depending on the industry and location. In India, this involves compliance with the Companies Act for corporate data, the Information Technology Act for digital data handling, and GST regulations for financial and transactional records.
Strategies to Ensure Accuracy and Compliance in Data Handling
- Regular Audits: Conducting periodic audits to check the accuracy of data and compliance with regulatory requirements.
- Training Programs: Regular training sessions for staff on the latest compliance standards and data management practices.
Leveraging Technology for Enhanced Data Management
Integration of Advanced Software Solutions
Investing in advanced software solutions that integrate seamlessly with existing systems can significantly enhance data management efficiency. Features to look for include AI-driven analytics for performance monitoring, automated compliance checks, and customizable reporting tools.
Benefits of Automation in Document Submission and Data Management
Automation reduces manual entry errors, speeds up processing times, and allows for better resource allocation by freeing up staff for higher-value tasks. It also improves scalability by handling increased data volumes without additional resource investment.
Future Trends and Best Practices
Emerging Trends in Vendor Data Management
The future of vendor data management is likely to see greater integration of AI and machine learning technologies, which can predict trends from data, enhance decision-making, and improve vendor selection processes.
Recommended Best Practices for Sustainable Vendor Relationships
- Transparent Communication: Open lines of communication with vendors to ensure expectations and requirements are clearly understood.
- Feedback Mechanisms: Implementing systems for collecting and acting on feedback from vendors to improve processes and relationships.