The journey towards digital transformation in India has reshaped numerous governmental processes, with driving licence verification emerging as a key area of innovation. Traditionally, this process was mired in paperwork and physical visits to transport offices, often leading to inefficiencies and delays. The advent of online verification represents a significant leap towards modernization, aligning with initiatives like Digital India aimed at simplifying citizen-government interactions.
About The Indian Driving Licence
The Indian driving licence (DL) is not just a legal document permitting its holder to operate various types of motor vehicles on public roads but also a vital identification tool embedded with numerous features for security, verification, and information purposes. Issued by the Regional Transport Offices (RTOs) across India, the DL comes with a standardized design and format that adheres to the regulations set by the Ministry of Road Transport and Highways.
Key Features of the Indian Driving Licence
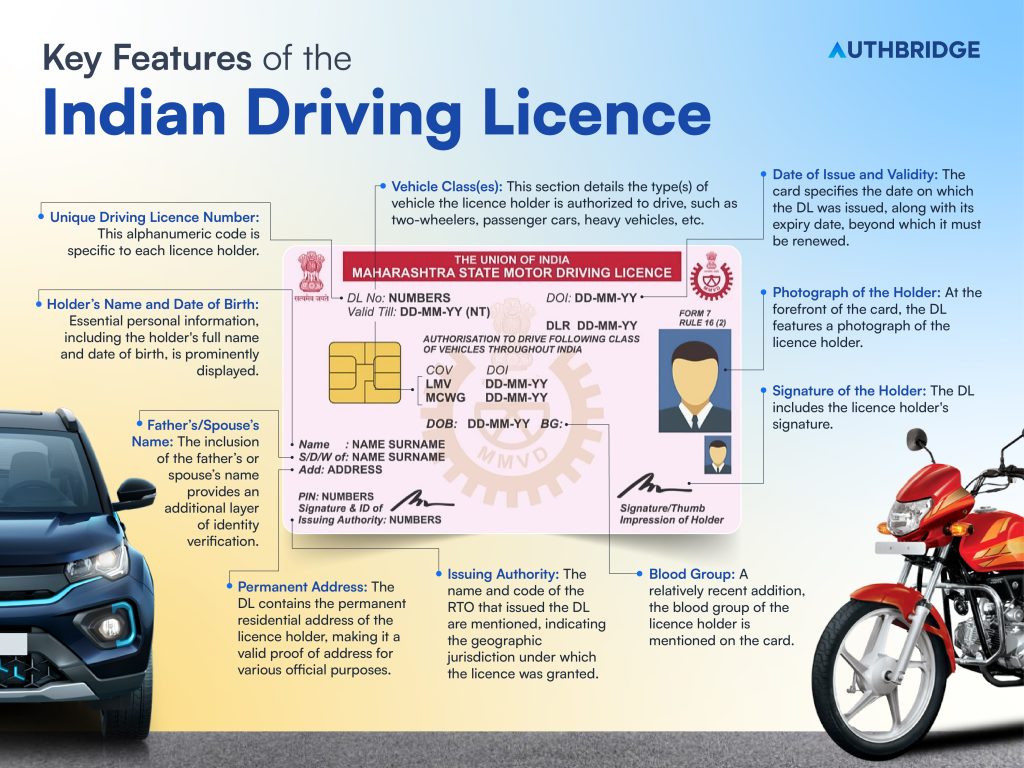
Let’s delve into the key features and details contained within an Indian driving licence:
- Photograph of the Holder: At the forefront of the card, the DL features a photograph of the licence holder, serving as a crucial identification mark.
- Unique Driving Licence Number: This alphanumeric code is specific to each licence holder, facilitating easy tracking and verification of the individual’s driving credentials.
- Holder’s Name and Date of Birth: Essential personal information, including the holder’s full name and date of birth, is prominently displayed, further aiding in identification.
- Father’s/Spouse’s Name: The inclusion of the father’s or spouse’s name provides an additional layer of identity verification.
- Blood Group: A relatively recent addition, the blood group of the licence holder is mentioned on the card, which could be critical in emergency situations.
- Permanent Address: The DL contains the permanent residential address of the licence holder, making it a valid proof of address for various official purposes.
- Issuing Authority: The name and code of the RTO that issued the DL are mentioned, indicating the geographic jurisdiction under which the licence was granted.
- Date of Issue and Validity: The card specifies the date on which the DL was issued, along with its expiry date, beyond which it must be renewed.
- Vehicle Class(es): This section details the type(s) of vehicle the licence holder is authorized to drive, such as two-wheelers, passenger cars, heavy vehicles, etc.
- QR Code: Modern DLs come with a QR code that, when scanned, directs to a digital verification page showing the licence’s authenticity and other details. This feature significantly enhances the security and ease of verification.
- Signature of the Holder: The DL includes the licence holder’s signature, providing an additional authentication method.
Countries Where You Can Drive With An Indian Driving Licence
Here’s the list of foreign countries where you can drive with an Indian Driving Licence: United States of America (USA), Malaysia, Germany, Australia, United Kingdom (UK), New Zealand, Switzerland, South Africa, Sweden, Singapore, Hong Kong, Spain, Canada, Finland, Bhutan.
Accessing Government Of India's Official Portal
To begin the verification process, individuals must access the official portal provided by the Ministry of Road Transport & Highways (MoRTH), Government of India – Sarathi Parivahan website. This portal serves as the gateway to a host of services related to driving licences, including application, renewal, and verification.
Benefits And Features Of Online DL Verification
The online Driving Licence verification process offers significant advantages over traditional methods:
- Efficiency: It eliminates the need to visit the RTO (Regional Transport Office) in person, saving time and reducing bureaucratic delays.
- Accessibility: Available 24/7, it allows for verification at any convenient time, making it highly accessible to users nationwide.
- Security: With advanced cybersecurity measures in place, users can rest assured that their personal information is protected against unauthorized access.
- Accuracy: Digital records minimize the risk of errors with manual data entry, ensuring the verification process is accurate.
The Significance Of Digital Verification For Driving Licences
Online DL verification stands as a cornerstone in enhancing the safety, reliability, and integrity of driver verification processes. It not only streamlines administrative operations but also elevates the level of access and convenience for the populace. This digital shift is pivotal in combating fraud, ensuring only qualified individuals are behind the wheel, thereby contributing to road safety and regulatory compliance.
In the rapidly digitizing landscape of India, online driving licence verification has emerged as a critical tool across various industries. This process not only enhances operational efficiencies but also plays a pivotal role in ensuring safety, compliance, and authenticity. Let’s explore the significance of online DL verification across different sectors in India:
Transportation And Logistics
In the transportation and logistics sector, the verification of driving licences is pivotal. It ensures that only qualified individuals operate vehicles, thereby reducing the risk of accidents and ensuring compliance with road safety regulations. For businesses, this verification process aids in building a reputable brand that prioritizes safety and reliability. Moreover, it streamlines the hiring process, enabling quicker validation of a candidate’s credentials, significantly reducing the administrative burden and expediting the onboarding of new drivers.
Car Rentals And Ride-Sharing Services
For car rental and ride-sharing companies, trust is a currency. Online DL verification ensures that drivers have valid licences, which is crucial for customer safety and trust. It also serves as a risk management tool, reducing the likelihood of incidents that could lead to legal liabilities. By leveraging digital verification, these companies can quickly onboard new drivers, ensuring they meet the safety standards required to provide a secure service to customers.
Financial Services And Insurance
In the realm of financial services and insurance, DL verification plays a critical role in fraud prevention and risk assessment. Insurance companies can use DL verification to prevent fraudulent claims by ensuring the policyholder’s driving licence is valid at the claim’s time. Similarly, financial institutions offering vehicle loans can assess the risk profile of applicants based on their driving records, leading to more informed lending decisions.
Employment Background Checks
For roles that require driving as a primary duty, employers leverage online DL verification to validate the authenticity of the credentials provided by applicants. This not only ensures compliance with regulatory standards but also safeguards the organization against potential liabilities arising from accidents involving unqualified drivers. Digital verification processes enable employers to conduct these checks efficiently, saving time and resources in the hiring process.
Hospitality And Tourism
In the hospitality and tourism industry, where employees often transport guests, verifying the driving licences of employees is essential for maintaining safety standards. It also protects the company’s reputation by ensuring that guests are in safe hands. Digital verification allows for quick checks, ensuring that all drivers meet the necessary legal requirements to operate a vehicle, thereby enhancing guest safety and satisfaction.
E-commerce And Delivery Services
The e-commerce boom has led to an increased demand for delivery services. Online DL verification ensures that delivery personnel are legally authorized to operate the vehicles they use, which is vital for maintaining service reliability and timeliness. It also helps e-commerce companies maintain high operational standards by ensuring their staff possess valid driving credentials, thereby reducing the risk of delays and accidents.
Education And Training Institutes
For driving schools and other educational institutes where driving instruction is provided, verifying the driving licences of instructors is crucial. It ensures that instructors are qualified to teach, enhancing the safety and quality of education provided to learners. Online verification processes provide a quick and efficient method for validating these credentials, contributing to a safer learning environment.
Manufacturing And Heavy Machinery
In industries that involve the operation of heavy vehicles or machinery, safety compliance is non-negotiable. Verifying the driving licences of operators ensures they are qualified to handle heavy machinery, thereby reducing the risk of workplace accidents. Online DL verification processes facilitate this by enabling quick checks of the validity and class of licences, ensuring operators are appropriately licenced for the machinery they operate.
Fraudulent Driving Licences In India
According to government data, it’s estimated that one in every three driving licences in India might not be genuine. Nitin Gadkari, the Road Transport and Highways Minister, highlighted that approximately 30% of the driving licences, out of a total of 180 million, are considered to be invalid, amounting to about 54 million potentially fraudulent licences. In India, about 32,000 driving licenses are issued daily.
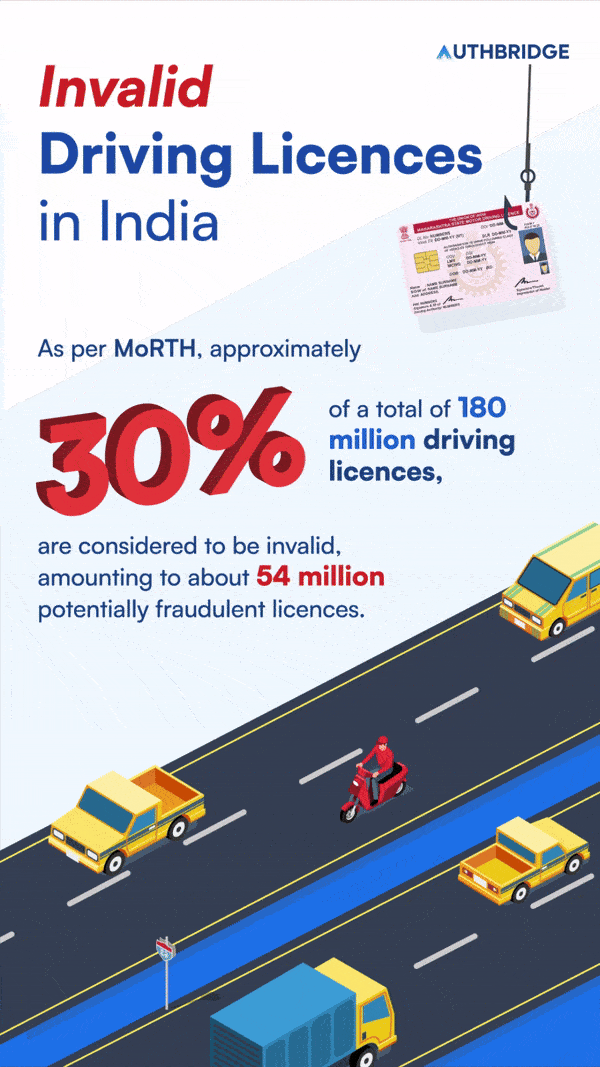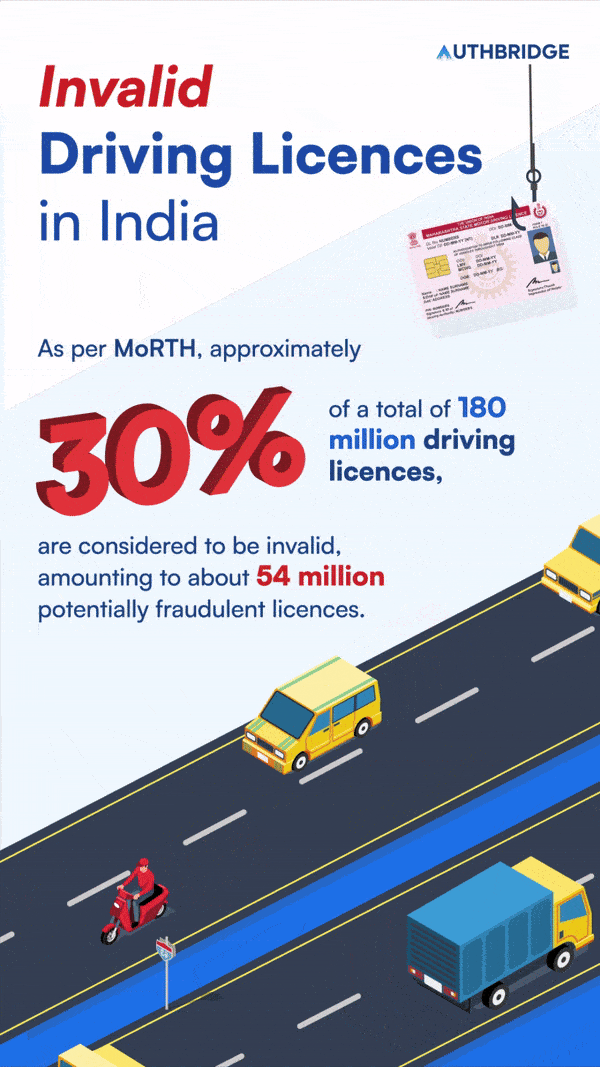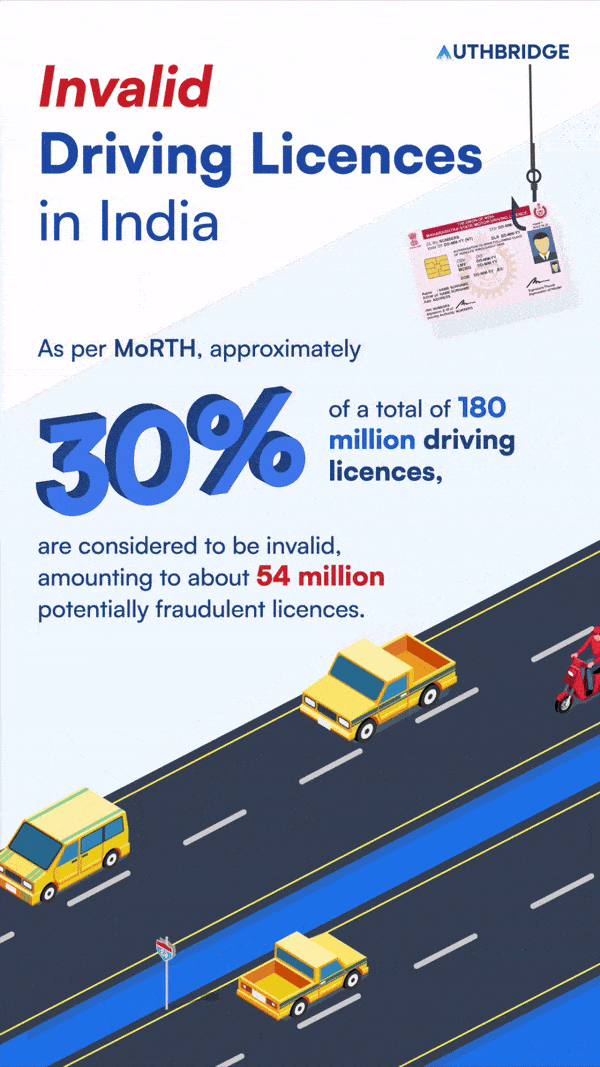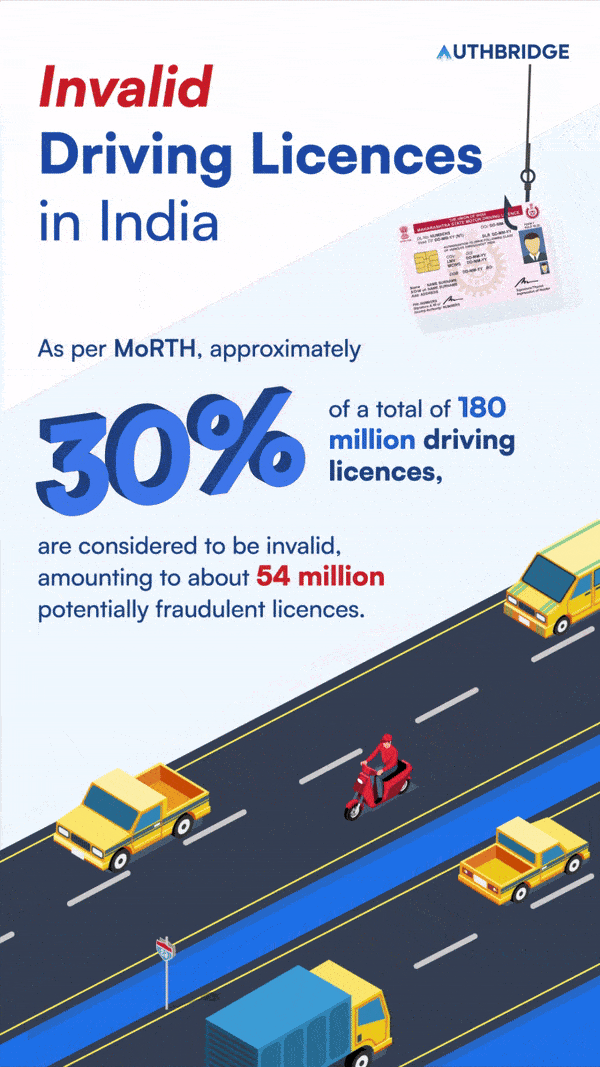
This prevalence of counterfeit or duplicate driving licences poses a significant risk of identity theft. This can severely impact the reputation and financial stability of businesses across various sectors. These include Shared Mobility, Delivery & Logistics, and Transportation. Identifying these fraudulent licences can be extremely challenging without specialized verification processes.
AuthBridge’s Driving Licence Verification API
Carry out real-time and seamless DL verification processes with AuthBridge’s driver licence verification API. Provide the image Driving licence or DL number as input to fetch instantaneous verification responses for the following data points.
- Name and image of the individual
- DL number
- DOB, age, and gender
- Category and type of vehicle authorized
- Issue and expiry timeline
- Address of the individual
- Issuing RTO Details
Screen out false licences/underage drivers and help onboard genuine customers, employees, drivers, and other third parties.
Top Reasons To Use AuthBridge’s Driver Licence Verification API
- Seamless Integration: Businesses often struggle with manual verification paperwork during high-volume recruitments and onboarding. Our industry-leading APIs will ensure seamless integration with your existing workflows and processes and speed up your onboarding process.
- Onboard new drivers/renters in a few seconds: You need to onboard individuals with a valid driving licence especially when you are onboarding drivers or vendors for your mobility, and logistics-related businesses. DLs should be authentic and should have not crossed the expiry date. Our verification APIs extract details of the vehicle/driver from DL and check the driver’s licence status for seamless verification.
- Safeguard your business from illegitimate drivers: Any individual sitting in the driving seat must possess a valid DL as with ‘driving’ also comes a sense of responsibility. Our Driver Licence Verification API helps businesses filter out bad actors, underage drivers, and fake/forged DLs before renting out a car, bike, or recreational vehicle.
- Real-time verification: The turnaround time of the API is very low, as low as 1 second, assuring real-time and instant verification of driving licence. With our instant DL verification API, you just need to enter the details of the DL or simply upload a photo of the DL. The OCR will extract the data and validate it with government databases in real time.
- Protection against identity frauds: Validate the authenticity of customers, employees, and third parties and detect document fraud and identity theft. Mitigate financial and reputational risks when onboarding drivers, delivery partners, vendors, renters, merchants, etc.
- Plug and Play APIs: Our industry-leading APIs ensure seamless integration with your existing workflows and processes
- Comply with regulations: Stay compliant with regulations i.e. KYC (Know Your Customer), AML (Anti-Money laundering), CFT (Counter-Terrorist Financing) Directive, GDPR (General Data Protection Regulation), etc.
About AuthBridge
With over 18 years of experience in the industry, AuthBridge has been at the forefront of creating databases, and building algorithms to enable instant searches to perform background checks without compromising on data security. AuthBridge is trusted by over 2,000 clients in 140 countries for their background check needs. Our database contains over 1 billion proprietary data records for conducting background checks. AuthBridge conducts an impressive volume of 15 million background checks every month.