Overview of TPRM in the Educational Sector
In recent years, India’s educational sector has witnessed a paradigm shift towards digital learning platforms, propelled by initiatives like the Digital India campaign and the unforeseen push from the COVID-19 pandemic. This shift, while revolutionizing the educational landscape, introduces significant cybersecurity risks and data privacy concerns, as institutions now depend more on third-party educational technology (EdTech) vendors for learning management systems, online content delivery, and student information management.
The Third-Party Risk Management (TPRM) in the educational sector involves a systematic approach to assessing, monitoring, and mitigating risks associated with external vendors, especially those providing EdTech solutions. It encompasses cybersecurity measures to protect against unauthorized access, data breaches, and other cyber threats, as well as ensuring compliance with data privacy laws to safeguard sensitive student information. For Indian educational institutions, embracing TPRM is not just about risk mitigation but also about building trust with students, parents, and regulatory bodies, ensuring the safe and effective use of technology in education.
The Cybersecurity Landscape in Educational Institutions
Common Cybersecurity Threats Faced by Educational Institutions
Educational institutions are increasingly targeted by cyberattacks due to the wealth of sensitive data they hold and their often-underprepared security infrastructures. Common threats include phishing attacks, ransomware, data breaches, and DDoS (Distributed Denial of Service) attacks. The challenge is magnified in India due to varied levels of cybersecurity maturity across institutions.
The Impact of Cybersecurity Breaches on Education
Cybersecurity breaches can have devastating effects on educational institutions, from disrupting learning processes to compromising the privacy of student and staff data. Financial losses, reputational damage, and legal consequences are significant concerns. Moreover, such breaches undermine the trust in digital education platforms, essential for the ongoing digital transformation in India’s education sector.
The Cybersecurity Landscape in Educational Institutions
Common Cybersecurity Threats Faced by Educational Institutions
The digital foray has left educational institutions vulnerable to a myriad of cybersecurity threats. In India, where digital literacy is burgeoning, these threats pose significant risks.
- Phishing Attacks: Often targeting unsuspecting students and staff with the aim of stealing sensitive information.
- Ransomware: Malicious software designed to block access to a computer system until a sum of money is paid.
- Data Breaches: Unauthorized access to confidential student and staff data, leading to privacy violations.
Table 1: Cybersecurity Threats and Their Impacts
Threat Type | Impact on Institutions |
Phishing | Loss of sensitive information, financial fraud |
Ransomware | Disruption of educational services, financial loss |
Data Breaches | Legal ramifications, loss of trust |
The Impact of Cybersecurity Breaches on Education
Cybersecurity breaches in educational institutions can lead to significant disruptions. Beyond the immediate loss of sensitive data, these breaches can erode trust among students, parents, and staff, potentially deterring engagement with digital learning tools critical for modern education.
Data Privacy Concerns in Educational Technology
The Importance of Protecting Student Information
The digitization of education requires the collection and processing of vast amounts of student data. Protecting this data is paramount, not only to comply with laws but also to maintain the trust and safety of students. In India, where data protection awareness is growing, institutions must be vigilant in their data privacy practices.
Regulatory Landscape for Data Privacy in Indian Education
The Indian Personal Data Protection Bill, once enacted, along with existing IT laws, outlines a framework for data privacy that educational institutions need to comply with. Understanding these regulations is crucial for TPRM strategies focused on educational technology vendors.
Developing a Comprehensive TPRM Strategy
Establishing a Governance Framework for Cybersecurity and Data Privacy
A governance framework for TPRM involves:
- Leadership Commitment: Ensuring top management’s commitment to cybersecurity and data privacy.
- Policies and Procedures: Developing comprehensive policies that address risk assessment, vendor management, and incident response.
Conducting Risk Assessments for Educational Technology Vendors
Risk assessments help identify potential vulnerabilities within third-party products and services. They should cover:
- Vendor Security Posture: Evaluating the cybersecurity measures implemented by vendors.
- Compliance Checks: Ensuring vendors comply with Indian data protection laws and international standards.
Implementing Cybersecurity Measures
Key Cybersecurity Practices for Educational Institutions
To safeguard against threats, institutions should implement:
- Secure Access Controls: Limiting access to sensitive information through robust authentication methods.
- Regular Security Training: Educating students and staff on recognizing and responding to cybersecurity threats.
Leveraging Technology for Enhanced Security
Advancements in technology offer tools for better cybersecurity:
- Firewalls and Encryption: To protect against unauthorized access and data breaches.
- AI-Powered Threat Detection: Using artificial intelligence to identify and mitigate potential threats in real-time.
Ensuring Data Privacy and Compliance
Strategies for Protecting Student Data include:
- Data Minimization: Collecting only the necessary data for educational purposes.
- Encryption: Ensuring that stored and transmitted data is encrypted.
Compliance with Indian and International Data Protection Laws
Educational institutions must navigate:
- Personal Data Protection Bill: Preparing for compliance with India’s upcoming data protection regulations.
- GDPR: For institutions dealing with international students, adherence to the GDPR may be necessary.
Challenges and Solutions in TPRM for Education
Navigating the Challenges of Digital Transformation in Education
Challenges include:
- Rapid Technological Changes: Keeping pace with the fast-evolving digital landscape.
- Vendor Management: Ensuring all third-party vendors adhere to the institution’s cybersecurity and data privacy standards.
Best Practices for TPRM Implementation
- Continuous Monitoring: Establishing mechanisms for the ongoing evaluation of third-party risks.
- Vendor Collaboration: Working closely with vendors to ensure they understand and comply with the institution’s cybersecurity and data privacy expectations.
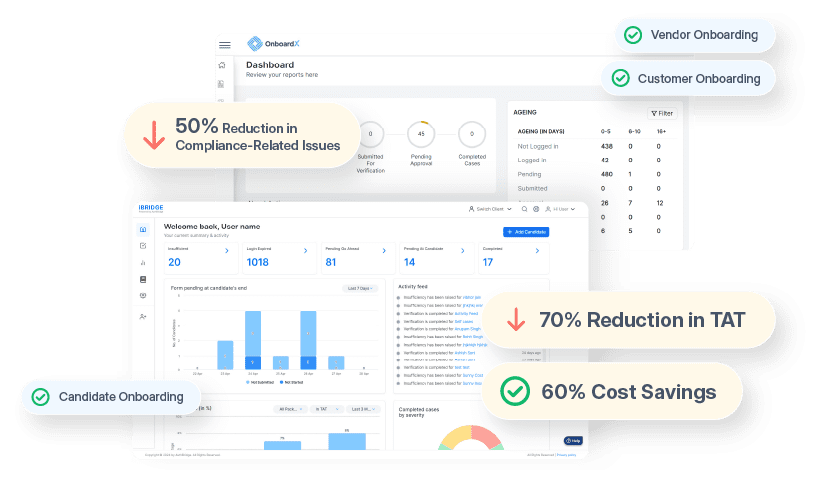
OnboardX By AuthBridge
Welcome to the Future of Vendor Management, OnboardX: The Comprehensive Platform for end-to-end Third-Party Onboarding and Verification. Say goodbye to the hurdles of inefficiency, data disparities, and regulatory complexities.
Adopt a path of automated processes, scalable operations, and cutting-edge analytics to elevate your vendor relationship management to new heights.
As leaders in the world of BGV and due-diligence, our one stop onboarding solution aims to provide seamless onboarding to organisations by offering features such as:
- Case approval workflow with payment and contract signing
- Custom communication options in emails and WhatsApp
- 160+ real-time checks and verifications
- Personalized and customizable solution
- Seamless API integration
- Fully automated journey with multiple touch points and clear visibility
Conclusion
In the digital age, the importance of TPRM in safeguarding the educational ecosystem against cybersecurity risks and ensuring the privacy of student data cannot be overstated. By adopting a comprehensive TPRM strategy, leveraging technology, and fostering a culture of awareness and compliance, Indian educational institutions can navigate the challenges of digital transformation, ensuring a secure and prosperous future for education in India.