Introduction
In today’s digital landscape, where data breaches can significantly impact an organization’s reputation and financial stability, ensuring the privacy and security of data managed by third parties has become paramount. For Indian businesses, navigating the complex web of national and international data protection regulations is a critical aspect of Third-Party Risk Management (TPRM).
The Importance of Data Privacy in the Digital Age
With the increasing digitization of business processes and the exponential growth of data, the importance of maintaining data privacy and security cannot be overstated. Inadequate data protection measures can lead to severe consequences, including legal penalties, loss of customer trust, and financial losses.
Overview of India's Data Protection Regulations
India is on the cusp of a significant regulatory shift with the introduction of the Personal Data Protection Bill (PDP Bill), aligning with global data protection standards such as GDPR. This evolving regulatory landscape emphasizes the need for businesses to reassess their TPRM strategies to ensure compliance not only with domestic regulations but also with applicable international standards.
The PDP Bill introduces comprehensive guidelines for data collection, processing, and storage, mandating stringent compliance requirements for businesses and their third-party partners. It highlights the necessity for a robust TPRM framework that actively manages third-party data privacy risks and ensures compliance across all data processing activities.
Strategic Framework for Third-Party Data Privacy Compliance
The establishment of a comprehensive TPRM policy specifically addressing data privacy and security is essential for businesses aiming to comply with India’s evolving data protection regulations. This policy should outline clear standards and expectations for third-party vendors, ensuring they understand and commit to maintaining high levels of data security and privacy.
Developing a Comprehensive TPRM Policy for Data Privacy
A robust TPRM policy forms the cornerstone of effective data privacy and security management. This policy should detail the processes for vendor selection, risk assessment, and ongoing monitoring, with a specific emphasis on data protection.
Key Elements to Include:
- Data Privacy Objectives: Align the TPRM policy with the organization’s data protection goals and compliance requirements.
- Vendor Selection Criteria: Outline specific data security and privacy standards that vendors must meet to do business with your organization.
- Risk Assessment Procedures: Define how risks associated with third-party vendors will be identified, assessed, and mitigated.
Establishing Data Privacy Standards for Third-Party Vendors
Setting clear data privacy standards for vendors is crucial. These standards should be communicated effectively during the onboarding process and embedded in all contracts and agreements with third-party partners.
Standards Implementation:
- Data Processing Agreements (DPAs): Ensure that DPAs clearly define the roles, responsibilities, and data protection expectations for both parties.
- Compliance with Local and International Laws: Vendors should be required to comply not only with Indian regulations like the PDP Bill but also with international standards if applicable.
Effective Onboarding and Continuous Monitoring
The onboarding process is a critical juncture at which data privacy and security expectations should be set. Following onboarding, continuous monitoring ensures that vendors remain in compliance with these standards.
Streamlining Third-Party Onboarding with a Focus on Data Security
A streamlined onboarding process helps in identifying potential data privacy risks from the outset. This process should include thorough vetting of the vendor’s data security practices and a clear communication of data privacy expectations.
Onboarding Best Practices:
- Vendor Verification: Perform comprehensive checks on the vendor’s data protection measures and past compliance record.
- Education and Training: Provide vendors with training on your organization’s data privacy policies and procedures.
Implementing Continuous Monitoring for Data Privacy Compliance
Continuous monitoring is vital for detecting and addressing any deviations from agreed-upon data privacy standards. This process should leverage technology to automate the tracking and reporting of compliance statuses.
Continuous Monitoring Techniques:
- Automated Alerts: Set up alerts for any breaches or non-compliance incidents reported by or about the vendor.
- Regular Assessments: Conduct periodic reviews of vendor practices and compliance through self-assessments, audits, and check-ins.
Leveraging Technology for Enhanced Compliance
Technological tools and platforms can significantly enhance the efficiency and effectiveness of TPRM processes related to data privacy and security.
Utilizing Vendor Management Software for Data Privacy Assurance
Vendor management software platforms can automate many aspects of TPRM, from onboarding to continuous monitoring, making it easier to manage and document compliance with data privacy standards.
Software Solutions:
- Digital Vendor Management: Platforms like Supplier Onboarding Software or Ariba help in managing vendor relationships, including compliance tracking and performance assessments.
- Integration with ERP Systems: Tools that integrate with SAP, Oracle, or other ERP systems can streamline data flow and enhance visibility into vendor compliance.
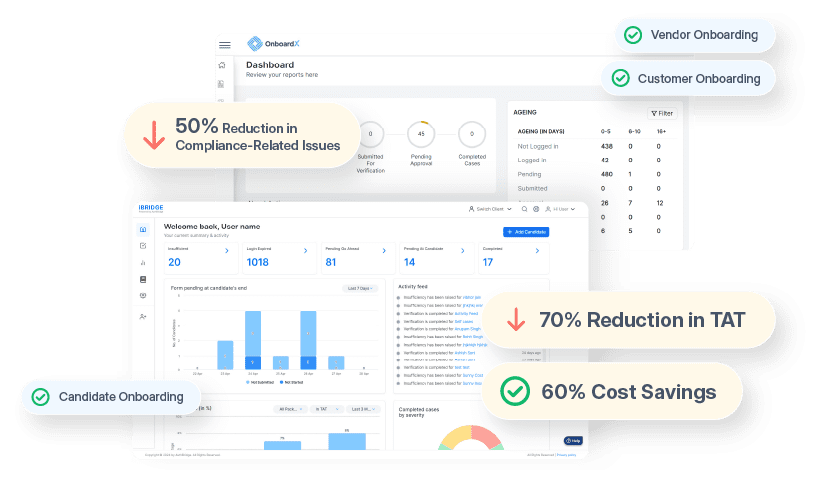
OnboardX By AuthBridge
Welcome to the Future of Vendor Management, OnboardX: The Comprehensive Platform for end-to-end Third-Party Onboarding and Verification. Say goodbye to the hurdles of inefficiency, data disparities, and regulatory complexities.
Adopt a path of automated processes, scalable operations, and cutting-edge analytics to elevate your vendor relationship management to new heights.
As leaders in the world of BGV and due-diligence, our one stop onboarding solution aims to provide seamless onboarding to organisations by offering features such as:
- Case approval workflow with payment and contract signing
- Custom communication options in emails and WhatsApp
- 160+ real-time checks and verifications
- Personalized and customizable solution
- Seamless API integration
- Fully automated journey with multiple touch points and clear visibility
Why Choose OnboardX?
OnboardX is a comprehensive one-stop solution for all your vendor onboarding needs and here a few reasons why we think it will be the best suited solution for your needs:
- Unmatched Flexibility: A low-code platform allowing fast, custom solution development with minimal technical skill requirements.
- Comprehensive Integration: Deep integration capabilities with major ERP and P2P suites, serving as a central third-party data layer.
- Advanced Third-Party Data Management: Expertise in managing complex and continuously changing third-party data, with more than 18+ years of enterprise experience.
- Targeted Solutions Over Generic Tools: Specific focus on third-party data, differentiating from generic P2P suites, MDM solutions, and in-house systems.
- Pre-Integrated APIs: Comes with pre-integrated APIs and proprietary databases for faster turn-around time and comprehensive verification processes
- Easy on Pockets: Consolidate data collection, verification, and signature processes into a single, budget-friendly solution. Say goodbye to fragmented expenses on multiple tools – OnboardX streamlines it all for the price of one.
- Dedicated Third Party Expertise: Dedicated team focused on vendor management solutions, ensuring specialised knowledge and tailored services.