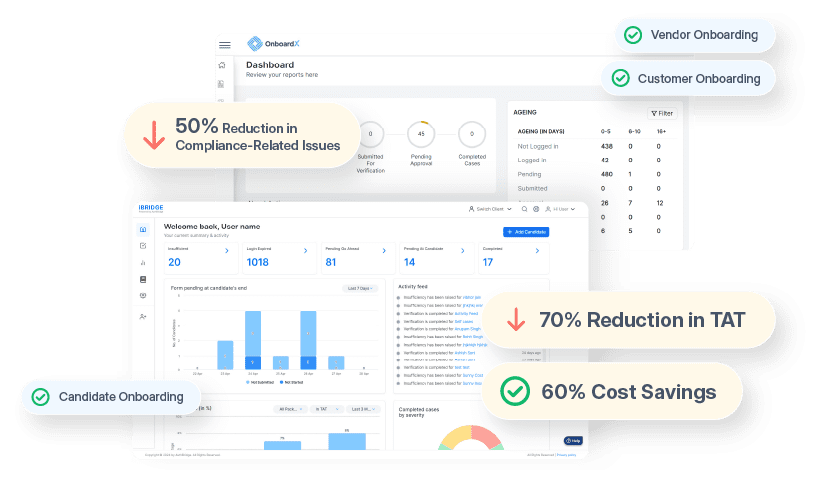
“Sensitive” is a word I hear all the time in the context of the work done by background verification companies. Random people one meets ask about our nature of work and, when told, their immediate response is that handling sensitive data and maintaining its integrity must be the backbone of the background screening business.
That hits the bull’s eye. If sensitive information is defined as something that must be protected against unwarranted disclosure, then the information that we in this industry generate is ultra-sensitive. It must be safeguarded for legal and ethical reasons, apart from individual privacy and proprietary considerations.
If information security in the context of background screening gets compromised, it has a severe effect on all three concerned parties — the employer loses proprietary data of current employees to competitors; the individual could have his personal reputation compromised; and, of course, the background screening company could find its hard-earned brand reputation in tatters. The challenge of information security is all the greater considering that it has to extend to all situations, ranging from physical theft to natural disasters. Hence, customers engaging the services of background screeners must look beyond pricing.
To gauge the efficacy of data protection in the background screening process, companies must ask themselves the following questions: – What are the physical and logical barriers to data access? – Is data access in the background screening company allowed strictly on a need-to-know basis? For example in my company, the verification teams are not privy to the name of the client(s) on whose cases they are working on at any point in time, thus ensuring a hard firewall. – Who in the background screener’s organization has access to negative reports? Not long ago, I interviewed a candidate who wanted a job with us after having worked with a competitor.
Nothing exceptional, right? Happens all the time. Well, this individual was carrying 50-odd candidate reports with him to help support his claim that his current employer was doing poor quality work. Imagine — 50 confidential and highly personal reports being bandied about in such cavalier manner. (Needless to add I did not meet this candidate again.) We need to also sensitize our clients on the need to be extremely careful about using sensitive information. A couple of years ago, one of our clients — easily among India’s top 50 companies — sent us a list of their employees whose background screening had to be initiated. The list should have contained employee IDs, name, email and contact address. That’s all.
The sheet we received had their compensation details too. Besides it had similar details of the top leadership hires done recently by the company. In dealing with confidential information, strict adherence to industry standards and government guidelines is a given, but my view is that confidentiality is more a culture-related thing — it goes beyond building technology barriers; it is about creating a culture in the company that respects data security and confidentiality. Organizations seeking enhanced information security should create a culture in which employees are loath to discuss sensitive information with anyone, no exception.
In the emerging global economy, background screeners will be required to continuously expand their business, which will require them to get into more collaborative efforts. As business grows and more collaborations take shape, information security will continue to assume greater importance. Clients will seek, and rightly so, tightening of controls and will need to know about how secure the data being shared across platforms is. In conclusion, I will say that accreditation to certifications related to information security systems will play a key role as our business grows and goes to the next level. However, information security and confidentiality must remain an article of faith for background screeners and those who work in our industry. Not a mere leap of faith.